Meet Alex, a seasoned data professional at a leading Fortune 500 company. He works in the bustling cityscape of Silicon Valley. It was a cool winter’s day when Alex suddenly found himself swimming amid a digital hell hole wherein his company’s AI threat detection capabilities reached an all-time low, right when they needed them the most.
His employer, which is outwardly revered for its innovation and market dominance, suddenly faced a novel type of network intrusion threat. The attack was subtle yet sophisticated, which allowed it to slip past traditional security measures as quietly as a burglar in the night.
The company’s confidential data was at risk, and so was his reputation. Alex’s heart immediately sank to the bottom of his chest when he saw the magnitude of the situation.
As a primary guardian of the company’s digital fortress, he felt the weight of a thousand boulders thrust upon his shoulders.
The tension in the boardroom was so thick, you could cut it with a knife. Stakeholders urgently voiced their dismay in ever so politically-correct terms.
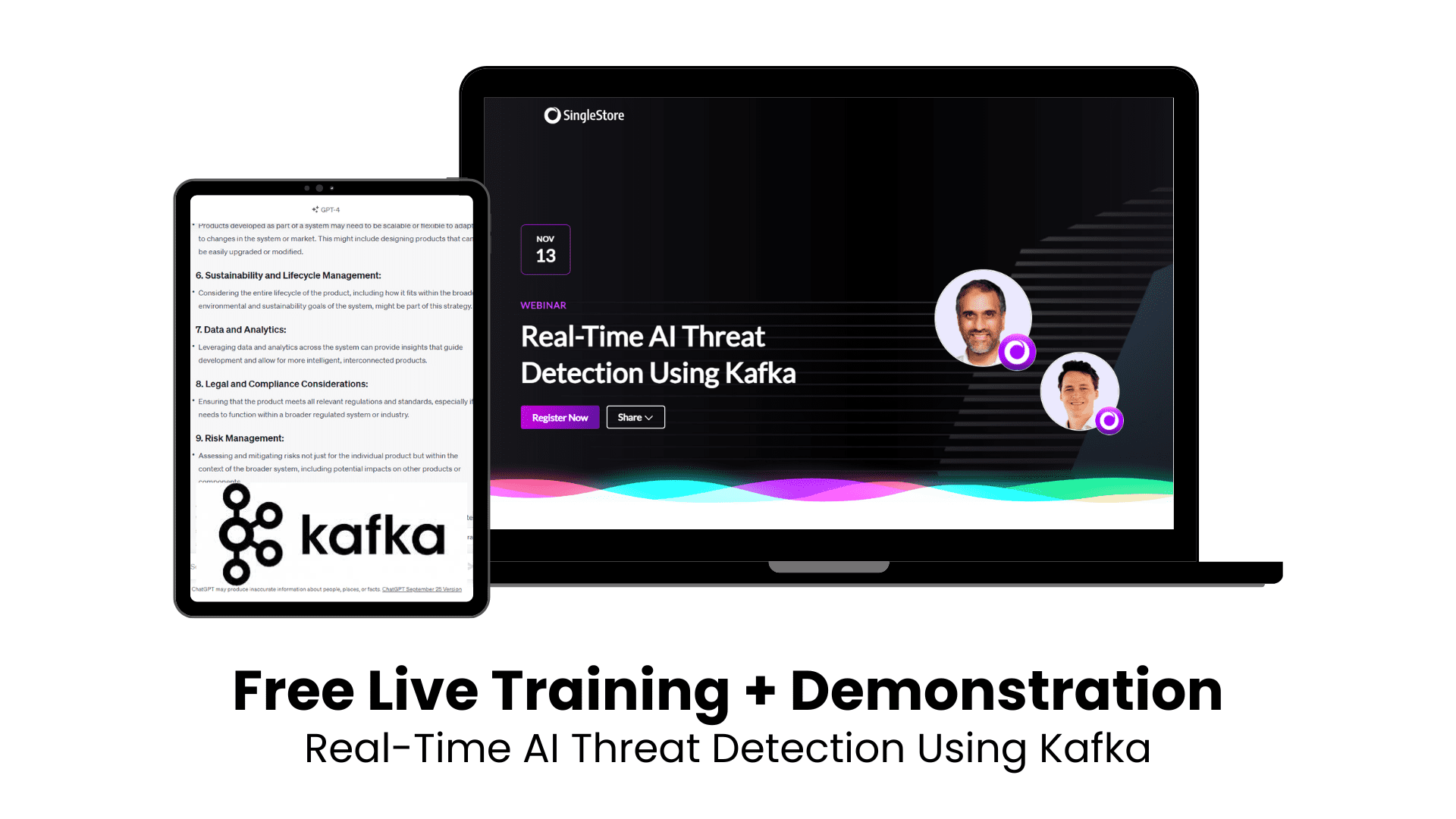
🔹Sign up for our free on-demand training on: Real-Time AI Threat Detection Using Kafka🔹
Alex’s team, a diverse group of skilled data pros, were all looking to him for direction. He could see the fear etched on their faces.
Alex proposed a bold solution – to deploy a deep learning model combined with similarity search in order to detect and mitigate the threat.
Alex was never one to succumb to pressure, though. He knows that within every problem lies an opportunity. Harnessing his deep AI and data science expertise, Alex proposed a bold solution – to deploy a deep learning model combined with similarity search in order to detect and mitigate the threat.
Of course, his plan was met with skepticism from some board members, for they really had no idea about the technical nuances of solving such a gargantuan problem.
Luckily, Alex’s strong data & AI strategy skills helped win them over pretty quickly.
After 48 hours of tireless work, Alex and his team developed a model that was capable of transforming network traffic data into vector embeddings. This innovative approach allowed them to represent network events comprehensively, turning abstract data into a readable map of digital footprints.
Fueled by a mix of coffee, determination, and the relentless pursuit of digital security, the days blurred into nights as the team refined their model.
As the model began to take shape, Alex felt a glimmer of hope. He watched in awe as the deep learning algorithm started identifying patterns in the data, patterns that were previously invisible to any human eye.
The similarity search component played a crucial role, pinpointing infrequent occurrences in the network traffic that signaled a potential breach – so that the company could then build automated systems to mitigate and eliminate potential threats.
Success didn’t happen overnight, of course.
Initially, the model produced false positives, sending Alex and his team back to the drawing board multiple times. Each setback was a blow to their morale, but Alex kept the team’s spirit alive with his strong leadership. He continually reminded them that in the world of cybersecurity, resilience is key.
Then it happened: One breakthrough evening, the model correctly identified and classified a malicious intrusion attempt.
The team’s hard work had paid off, and the threat was neutralized before it could inflict any real damage. The boardroom, once a place of absolute anxiety and despair, suddenly erupted in a chorus of relief and commendation.
Alex’s innovative approach had not only averted a potential disaster but also set a new standard in network security for the company!
In the end, Alex emerged as a champion data professional in the eyes of stakeholders. He was rewarded handsomely and expeditiously with a five-figure performance bonus.
AI threat detection: A look under the hood…
In Alex’s case, deep learning and similarity search played crucial roles in solving this network intrusion security event.
Here’s how it worked:
The deep learning component
Alex’s team employed a deep learning model for AI threat detection to analyze the vast and complex network traffic data. This model, which was trained on historical data, learned to recognize patterns and anomalies in network behavior. Its strength lay in its ability to process and interpret large volumes of data much faster and more accurately than any human could. It identified subtle signs of intrusion that would otherwise go unnoticed.
The similarity search component
Alongside deep learning, similarity search was a key tool in the AI threat detection solution as well. It worked by comparing new network events with known patterns of intrusion, looking for similarities that might indicate a threat. This method was particularly effective in identifying rare or novel intrusion attempts that didn’t match traditional malware signatures. By measuring how closely new network traffic matched these known intrusion patterns, the system could flag potential threats for further investigation.
Together, deep learning and similarity search provided a dynamic and robust defense mechanism against network intrusion, allowing Alex’s team to detect and mitigate threats in real-time, ensuring the security and integrity of their network.
Together, deep learning and similarity search provided a dynamic and robust defense mechanism against network intrusion, allowing Alex’s team to detect and mitigate threats in real-time, ensuring the security and integrity of their network.
If you’re ready to position yourself for the same type of success that Alex delivered here, I’ve got an amazing free training resource to share with you today!
Free on-demand training: Real-time AI threat detection using Kafka
In today’s digital landscape, the difference between a secured network and a compromised one can be mere seconds. That’s why you need real-time AI threat detection using Kafka.
Our upcoming free 1-hour on-demand training, “Real-Time AI Threat Detection Using Kafka,” is an event you cannot miss.
With the relentlessness of today’s cyber threats, traditional security measures are wholly inadequate. The integration of Kafka with advanced AI threat detection techniques offers a robust solution to detect and counteract these threats as they happen.
During this intensive session, you will witness a hands-on demo and code-share that will revolutionize your understanding of network security.
We’ll dig into the utilization of a deep learning model and similarity search, both of which are crucial in transforming network traffic data into comprehensive vector embeddings.
This approach is a game-changer in identifying and categorizing network intrusion traffic, allowing for real-time, accurate threat detection, mitigation, and elimination.
Imagine the impact you can make on your organization’s security when you can:
- Set up Kafka for real-time data processing and immediate threat detection.
- Apply SingleStoreDB’s advanced similarity search to pinpoint rare occurrences in network traffic, which often signify a breach.
- Transform network traffic data into vector embeddings, which is a vital step in effective similarity measurement and threat identification.
- Construct a network intrusion detection system capable of categorizing events as benign or malicious, thereby enhancing your network’s resilience against cyberattacks.
This training is not just about learning new skills; it’s also about empowering yourself to be on the forefront of cybersecurity defense. By participating, you’ll gain hands-on experience and insights that are crucial in today’s fast-paced, constantly evolving digital environment.
Secure your spot now for this groundbreaking training, before we take it down. This is your opportunity to stay ahead in the cybersecurity game and safeguard your organization’s digital assets.
** This how-to training was delivered live and is now available here on-demand **
Register for the “Real-Time AI Threat Detection Using Kafka” training now.
Don’t miss out on this chance to elevate your skills and to network with industry experts. Remember, knowledge is power, especially when it comes to cybersecurity.
Pro-tip: If you like this training on AI threat detection, consider checking out other free AI app development trainings we are offering here, here, here, here, here, here,here, and here.
See you there!
Lillian
P.S. If you liked this blog, please consider sending it to a friend!
Disclaimer: This post may include sponsored content or affiliate links and I may possibly earn a small commission if you purchase something after clicking the link. Thank you for supporting small business ♥️.